
Reputation: 2879
TCP protocol instead of SSL/TLS in Wireshark
I am trying to use .NET implementation of SslStream by this tutorial.
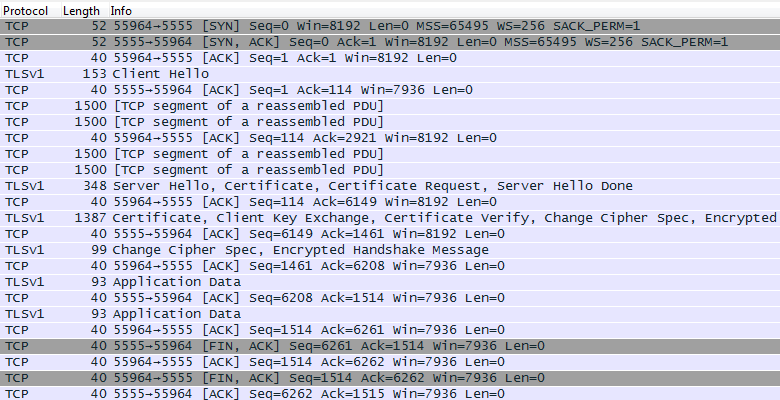
I did everything like in this article, but I have some question. I downloaded RawCap and captured packets from the localhost, after that I opened dump file(.pcap) using Wireshark, but instead of SSL or TLS type of protocol, I saw just TCP:  Here is the part of the TCP stream:
Here is the part of the TCP stream:
....l...h..T...........Y.2..1...t.4....8.J...../.5... ....... .2.8.......'..............SslServer. ......................M..T...M.<.......e.E
...M.%c...Kg.. .....iKku.^q(C.$..;..Mx......g&./..................0...0.............L.^..F.)...{.0...+......0.1 0...U....MyCA0.. 150228143257Z. 391231235959Z0.1.0...U....SslServer0.."0 ..*.H.. ..........0.. ......p9.cq...F.^....Bm...S... .....Bg.B.<]..f[...<...q'..Tc......R...Z.C.D.D...N...1..0.v..l.<...d[=C.7.8.+^..j(...X.........D'.!*5.^.^Ef..=.6y@.=..)|...Sp..Sv.|h.-..UT..&bG.......J{.7k.X...........:.[o....o.,r.......0..Wi.s.[email protected].....@.. ...f...0.1 0...U....MyCA..(J..j+..K......0...+...........h..X.+.M..{...n.....@.'[email protected],>.9.DE.R.V4t._bGY.,v.>G......J [email protected],%[S._..u...$....!V.r....~...'.~..T*[.#[.?.B{..Z..m.p.9.7.U.u.}.e..c..H^n.:...-AJxs.. ...:... ..u.....YB....2n...y.g=...(.Fv...B.Is..GK.....;.F..Ln.....L...ao [email protected]. ..AddTrust AB1&0$..U....AddTrust External TTP Network1"0 ..U....AddTrust External CA Root..0..1.0...U....US1.0...U. . GeoTrust Inc.1907..U...0(c) 2008 GeoTrust Inc. - For authorized use only1604..U...-GeoTrust Primary Certification Authority - G3.g0e1.0...U....US1.0...U.
Is this correct SSL/TLS stream? And why Wireshark marked it like TCP?
UPD:
Upvotes: 6
Views: 6433
Answers (1)

Reputation: 353
By default Wireshark uses TCP port numbers to know if this is standard TCP or TLS/SSL.
If you want to make Wireshark permanently recognize any port as SSL/TLS, then go to Edit > Preferences > Protocols > HTTP > Under SSL/TLS Ports change it from 443 to 443,5555, ... <other TLS/SSL ports go here>.
Also note that SSL traffic is encrypted, and that is why you won't be able to see the actual data being transmitted. If you want Wireshark to decrypt SSL traffic, then you will have to give it your server's private key (reference SSL dissection in Wireshark)
Upvotes: 7
Related Questions
- Decrypting SSL/TLS traffic from a app with Wireshark
- SSL has disappeared in wireshark
- Wireshark is not displaying http and https packets
- Cannot decrypt HTTPS Traffic with Wireshark
- SslStream without certificate
- Decrypt client-side SSL traffic in Wireshark generated by Java HttpsURLConnection
- Decrypting HTTPS traffic in Wireshark not working
- Wireshark doesn't show SSL packets with Python SSL sockets
- Why aftr the SSL program (client/server openssl) Wireshark shows me the protocol X11 & TCP and not SSL or TLS?
- How to Send SSL Packets captured with Wireshark?