
Reputation: 12245
Call SharePoint REST API from Teams Tab
I have a Teams Tab application that needs to do some manipulations with the team's site. The User needs to be authenticated, and all operations are executed on behalf of the user.
Calling the graph API is somewhat documented, I have found a good article here for example: https://bob1german.com/2020/08/31/calling-microsoft-graph-from-your-teams-application-part3/
But I want to call SharePoint REST API directly, not through the graph API because I want to do some operations that are not supported by graph API (yet?), like creating a page.
How can I achieve this?
As far as I understand I need to exchange the token I get from teams to another token that can be used to call SharePoint. (on_behalf_of flow). I added the scopes for SharePoint to the app registration, and requesting those when exchanging the token (https://microsoft.sharepoint-df.com/AllSites.Read for example). But I keep getting 401 access denied.
Please note that this is NOT about calling graph API. This is about the "normal" SharePoint REST API. For calling graph API it works.
More details and REST calls: https://gist.github.com/nbelyh/ec17a4e398069e35c2a2a5dc4447fb2a
Upvotes: 0
Views: 1710
Answers (3)

Reputation: 12245
Thank to @JeremyKelley-Microsoft for the answer, just posting it here for others:
You need to use https://{tenant}/AllSites.Read (or https://{tenant}/.default) as a scope, it DOES work. The {tenant} is the customer's tenant. Here is the flow:
0. Application registration permissions
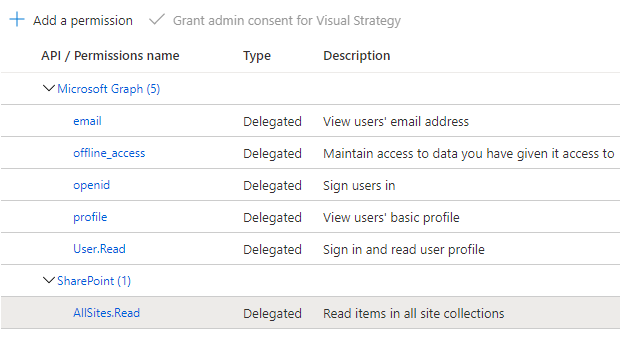
1. get the token from teams
microsoftTeams.authentication.getAuthToken() => <teams_token>
2. trade for graph token (on-behalf-of flow)
POST https://login.microsoftonline.com/{tenant}/oauth2/v2.0/token
client_id: <**your client id**>
client_secret: <**your client secret**>
grant_type: urn:ietf:params:oauth:grant-type:jwt-bearer
assertion: <**teams_token**>
requested_token_use: on_behalf_of,
scope: https://{tenant}/AllSites.Read
=> returns the <access_token>
3. use access token to access sharepoint REST API (get root site)
GET https://{tenant}/_api/web
headers:
authorization: "bearer " + <access_token>
Upvotes: 1
Reputation: 37710
I'm not sure if it matters regarding the "on behalf flow" vs "app only" flow, but from my experiments, aquiring tokens for graph call isn't same as acquiring token for SP rest call.
Specifically, endpoints aren't the same. Here's how I execute rest request from insomnia:
I guess the key is to use https://accounts.accesscontrol.windows.net/{{ tenantId }}/tokens/OAuth/2 instead of https://login.microsoftonline.com/{{ tenantId }}/oauth2/v2.0/token
Upvotes: 1
Reputation: 16066
In my opinion, SharePoint api could be accessed via access token through a http request. So if you've achieved the feature of calling graph api, I think the operation is similar. First, create azure ad application and create client secret, then you need to add application according to the api you need to call, finally, using client credential flow or any other suitable flow to generate the access token.
Or you mentioned 'not through the graph API' means what I said above? If I misunderstand someplace, pls point it out, and I think it's better to tell us which api you'd like to call.
==========================UPDATE============================
According to the link you provided in the comment, I found the apis in it(e.g GetSite: https://graph.microsoft.com/v1.0/sites/root) requires the api permission of 'graph->Sites.ReadWrite.All'(they are all graph apis), so when you generate the access token, you need to add it in the scope, and of courese, you need to add the api permission first in azure portal. Then you could call the api.
Upvotes: 0
Related Questions
- Microsoft Teams - how to get auth-token for api calls
- How to get the teams that a user belongs to using Azure Devops REST API?
- How to get access token for Azure DevOps from Microsoft Teams app?
- Microsoft Teams Authentication
- Calling an external API from MS Teams chat
- Basic Authentication instead of AAD (Azure Active Directory) Authentication
- What API do I use with the permissions my Teams app received in App Studio?
- How do I Call Microsoft Teams OnlineMeeting endpoints via Microsoft Graph API using a console app?
- How to fetch TeamId?
- Accessing user presence with REST API for Microsoft Teams




