Reputation: 20761
SQL Injection MySql in php
I've to make a small demonstration about how to make a MySQL Injection and how to protect us against them. I already know exactly how to protect our application for then, but I've some question about SQL injection.
A created a simple dummy website for the demonstration, on which I've added a search field. This search field isn't protected so subject to SQL injection.
I already made some example, like how to retrieve some global info on the database(version, current user, database name), inserting a " 'UNION SELECT [MyInteresstingFields] From [mytable]; --", but my question is:
What is the next step? Is it possible to alter the database? How? I don't see, because mysql_query(it's a php website using cakePhp) only runs one request, so how alter a SELECT request to make a change in the database?(e.g. insert, edit or anything else, doesn't matter, it's only to show them what can be the result).
Upvotes: 2
Views: 1952
Answers (4)

Reputation: 71
if your intention is to alter data in MySQL with sql injection without administrative privileges then you **can't ** . Although it's possible with SQL server . . 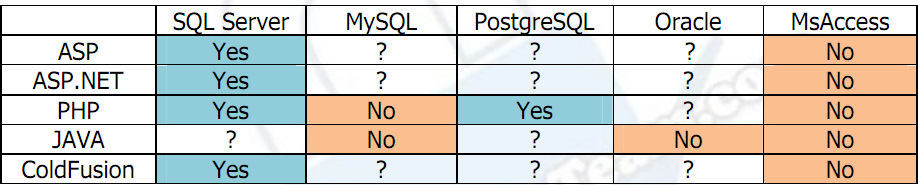
Upvotes: 2

Reputation: 26739
mysql_query() executes only one query exactly for the purpose to protect you from alter/drop/insert/update/delete statements if you are vulnerable to sql injection. But what if the vulnerable code is INSERT, UPDATE or DELETE statement? Then you can delete all rows, modifying the where, or maybe you could add another row, if you can add '), (<values>)' to the query, or you can update the access_level of the user, even if the original query updates only the password (if the password field is not escaped, and user enters ", access_level=1 for the password
Upvotes: 3
Reputation: 26783
Usually you will use the injection to collect admin passwords (or the token emailed via a password reset page), then login to the admin part and do the stuff from there.
Upvotes: 5
Related Questions
- How can I prevent SQL injection in PHP?
- SQL injection attack with php
- How do I prevent sql injection with php and mysql
- Security PHP login SQL injection
- SQL Injection for My PHP Site
- Injection attack by sql query in php
- PHP mysql injection protection
- PHP and SQL Injection
- SQL Injection Protection
- sql injection in php